I am currently pulling over groups from onelogin for entitlements. They are correctly populating in ISC. The issue I am running into is that when I select a user the portion that states the attributes for onelogin_role is empty. I was referencing this but still does not work, Loading Entitlements - SailPoint Identity Services
Could you please share the screenshot of account and entitlement schema?
See below @GOKUL_ANANTH_M
Hi @gbro ,
Which connector are you using?
Things to Validate
-
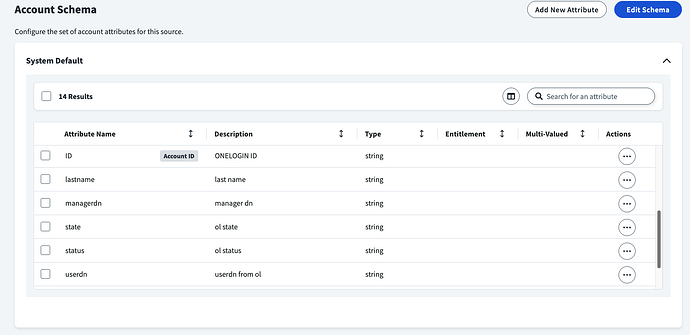
Account Schema
-
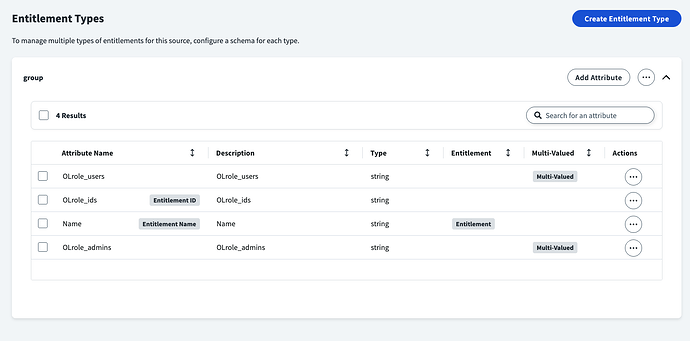
You’ve got an attribute called
onelogin_role. -
Marked as entitlement (good).
-
But: make sure the data type is either
single-valued/multi-valued.- If OneLogin sends back multiple roles per user, you need multi-valued here.
-
-
Entitlement Schema
-
Attribute
Namemarked as entitlement. -
But: ISC expects the Account schema entitlement attribute (
onelogin_role) to reference the same field as the Entitlement schema “display” (usuallyNameorid).-
Example:
-
If account data returns
role_id=12345, then the entitlement schema should also have an attribute with thatidvalue. -
If account data returns role
name=Admin, then the entitlement schema needs aNameattribute =Admin.
-
-
If these don’t align, ISC can’t populate user → entitlement.
-
-
Connector Response
-
Check the raw account payload ISC is getting during aggregation (you can do this via VA or by inspecting your OneLogin connector response in logs).
-
Look for what field actually carries the roles. Example:
{
“id”: “user123”,
“email”: “``test@domain.com``”,
“roles”: [“Admin”, “HR Manager”]
}
If it’s coming as “roles”, then your Account schema should have:Attribute name: roles
Marked as entitlement
Not onelogin_role unless you rename it in the schema mapping.
-
Thanks!
Not to sure about connector?
Also I was given some Java code for SailPoint IdentityIQ WebServicesAfterOperation (WSAO) rule written in Java/Groovy style. It runs after an account aggregation from OneLogin. Its purpose is to attach OneLogin role memberships to the aggregated account objects in IdentityIQ.
Hi @gbro,
Welcome to the SailPoint Developer Community.
Seems to me you are using a Web Services connector in SailPoint ISC to connect to OneLogin API from the provided screenshots. When I referred User endpoint of OneLogin API, there is no default attribute named onelogin_roles. Perhaps this is a custom attribute.
Try calling your OneLogin API using Postman to see the exact results, here is the Postman collection in case you need it. With the API response you can make sure the attributes are mapped correctly in HTTP Operation of the Web Service Connector.
Next would be to verify the logic in WebServicesAfterOperation rule if it’s attached to the source. WebServicesAfterOperation rule could be used to add additional attributes from endpoints different from /Users to form a complete account object/response.
This topic was automatically closed 60 days after the last reply. New replies are no longer allowed.