Hey guys
For the Active Directory source, we are using some attributes on the update provisioning policy.
One of them is the ‘description’ attribute, which needs to change depending on the user’s lifecycle state.
{
"name": "description",
"transform": {
"type": "static",
"attributes": {
"dataAtual": {
"attributes": {
"expression": "now-3h"
},
"type": "dateMath"
},
"cpf": {
"type": "identityAttribute",
"attributes": {
"name": "cpf"
}
},
"situacao": {
"attributes": {
"name": "situacao"
},
"type": "identityAttribute"
},
"lcs": {
"attributes": {
"name": "cloudLifecycleState"
},
"type": "identityAttribute"
},
"value": "#if($lcs == 'ativo')$cpf#elseif($lcs != 'desligamentoIntempestivo' )$situacao - $dataAtual pelo Sailpoint#{else}Desligamento intempestivo - $dataAtual pelo Sailpoint#end"
}
},
"attributes": {},
"isRequired": false,
"type": "string",
"isMultiValued": false
},
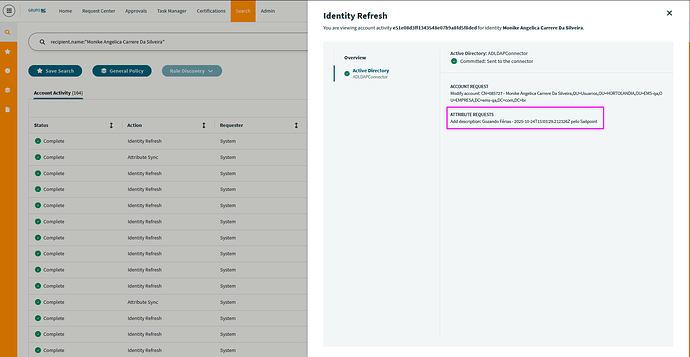
However, we noticed that whenever an update occurs, multiple “Modify Account” events are created, even if the attributes are updated only once.
Here we can see 4 requests trying to update the ‘description’ attribute:
All of them were opened at 03:03 PM, with the only difference being the seconds.
How does the update provisioning policy work? Should we create an identity attribute and use attribute sync on the source instead?