This enhancement is brought to you by
Idea GOV-I-489
Description
With this release, we’ve added the ability to automatically delete accounts through Lifecycle Management on supported downstream connectors. This highly requested capability (323+ votes in the Ideas Portal) eliminates the need for custom BeforeProvisioning rules. All lifecycle state changes and account deletion operations are fully audited, ensuring security and compliance.
Problem
When an identity is terminated, disabling accounts may not be enough. Many organizations require true deletion of accounts to meet compliance requirements and prevent identity reuse.
Today, admins must rely on BeforeProvisioning rules to perform deletions. This creates deployment friction, increases reliance on services or partner resources.
Solution
Admins can now configure Lifecycle States to delete accounts in addition to enabling and disabling them. This option is intentionally restricted to inactive long-term identity state to reduce risk and ensure deletions are deliberate. The configuration can be found under:
Admin → Identity Management → Identity Profiles → [Select Identity Profile] → Lifecycle Management → [Select Lifecycle State]
For disconnected sources, the system generates a manual task and sends an email notification so the source owner can complete the deletion.
When an account is deleted, any associated entitlements that are linked to account are removed from the identity. If the identity still has a role assigned that includes entitlements on sources that selected for deletion, ISC will delete the account, but it will be recreated on the next identity refresh because of the active role assignment. To avoid this, we recommend removing any related Roles from the identity before deleting its accounts. Accounts are not deleted if the source also has Access Profiles listed under the Access Profiles tab.
All account deletions and configuration changes are fully auditable. Auditors can see who enabled account deletion, when it was enabled, and which sources were selected. Identity Security Cloud emits Delete Account events, recording key attributes such as the source, account identifiers, timestamp, actor, entitlements, and any error messages if the action fails.
Scope of this release:
- Most sources are supported for account deletion via Lifecycle Management in this release, with additional source coverage planned for next quarter.
- To see which sources currently support account deletion, please refer to this page: Identity Security Cloud Connectors (publish date: September 16th). > On this date, the Account Operations column will include D (Delete), indicating which connectors support account deletion.
- The All Sources option in UI will remain disabled until delete is supported across all applicable connectors.
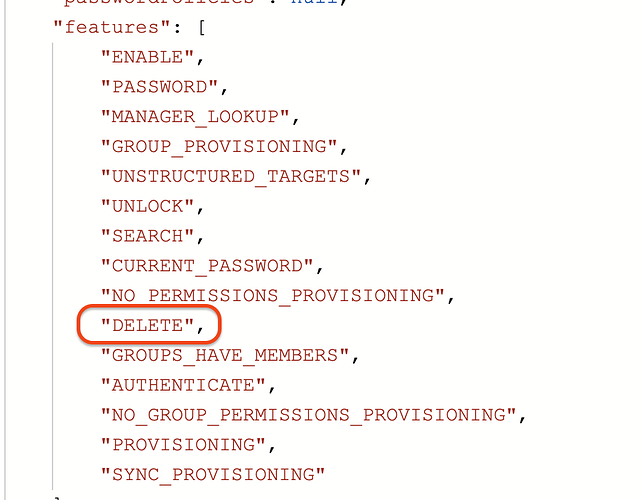
- Supported sources will display “delete” in their feature array when calling the List All Sources endpoint.
 Important
Important
Accounts deleted through Lifecycle Management cannot be restored. Once an account is permanently removed, the only way to regain access is for the identity to be re-provisioned through standard access requests or role assignments. Administrators should carefully review lifecycle configurations before enabling deletion to ensure this action aligns with organizational policies and compliance requirements.
Who is affected?
All Identity Now and Identity Security Cloud customers.
Action Required
To take advantage of this new capability, we recommend that administrators review their Lifecycle State configurations under:
Admin → Identity Management → Identity Profiles → [Select Identity Profile] → Lifecycle Management → [Select Lifecycle State]
From there, you can:
- Enable Delete Accounts for termination lifecycle states.
- Review which sources currently support deletion by using the Specific Sources chooser.
- Test the configuration in a sandbox environment before applying changes to production.
Important Dates
Calendar
By RSVP’ing to this event you will be reminded of this release prior.
- Sandbox Rollout: September 15th, 2025
- Production Rollout: The week of September 22nd, 2025.