Capability 1: CIEM MIS
Description
CIEM MIS provides effective access visibility into Azure Service Principals and Google Cloud Service Accounts.
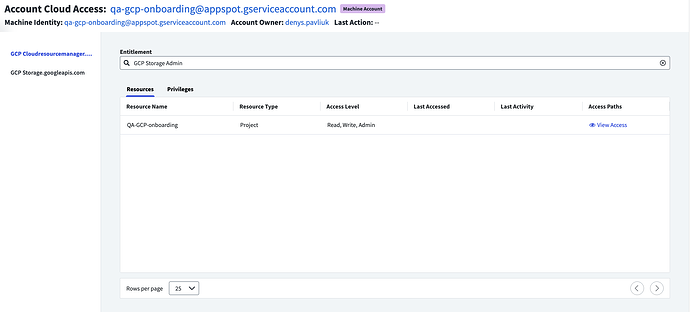
Since the launch of MIS, CIEM customers have asked for CIEM visibility to help manage risk from cloud machine accounts. Previously, customers could only view the Service Principle or Service Account entitlement assignment. CIEM effective access did not include the cloud service access.
With CIEM MIS, customers can better maintain least privileged cloud-access. Customers can view the full access path from the entitlement through cloud RBAC to the cloud services. Customers also can view ALL the access paths to the cloud services. CIEM MIS helps customers right size cloud Machine Account access.
Problem
IAM admins and machine owners currently can’t see what cloud services Azure and GCP machine identities can access, which hinders both decision-making and right-sizing efforts.
Solution
CIEM MIS
Azure Service Principal Entitlement Path
Service Principle All Paths
Service Account Entitlement Path
Service Account All Paths
Who is Affected?
CIEM customers who also own MIS.
Action Required
No action required.
Capability 2: CIEM AIC - Cloud Privilege Heat Map widget
Description
Customers have praised CIEM AIC for combining identity data with cloud access data. AIC customers with authoring capabilities and cloud knowledge could create insightful dashboards. However, IAM teams have asked for more out-of-the-box simplicity to quickly identify potential risks.
CIEM’s Cloud Privilege Heat Map plots identities by their number of entitlement assignments and accessible resources. IAM teams can then target these identities and evaluate their organizations access models. IAM teams can then work even closer with cloud teams to right-size entitlements ensuring identities have only the required cloud access.
Cloud Privilege Heat Map expedites customers ability to right-size access and reduce risk.
Problem
Customers were challenged to identify identify identities with potentially over-privileged cloud access.
Solution
Who is Affected?
CIEM customers who own Access Intelligence Center (AIC)
Action Required
No action required
Capability 3: Source Scope Insights My SailPoint widget
Description
Cloud Providers have logical divisions in their cloud such as Azure subscriptions, AWS accounts, and GCP projects. These sub-sources or ‘scopes’ frequently change. Customers wanted to know if CIEM is collecting all the sub-source data to ensure proper cloud access governance.
Problem
Ensuring CIEM sources are collecting all the sub-sources in AWS, Azure, and GCP cloud infrastructure.
Solution
CIEM Source Scope Insights widget.
Who is Affected?
CIEM customers.
Action Required
No action required.