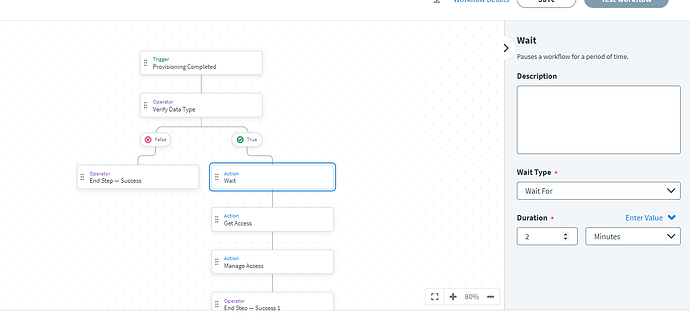
Though this is the logic for your workflow, I am not sure how effective this whole operation will be as I am not entirely sure about chronology of Provisioning, Single Account Aggregation / Account Aggregation and Deprovisioning - post execution of the workflow
Here is my explanation
If you look at the json sample for Provisioning Completed Trigger in this page you will see it returns the accountRequests details as an Array as shown below:
"accountRequests":[
{
"source":{
"id":"4e4d982dddff4267ab12f0f1e72b5a6d",
"name":"Corporate Active Directory",
"type":"SOURCE"
},
"accountId":"CN=example,ou=sample,ou=test,dc=ex,dc=com",
"accountOperation":"Modify",
"provisioningResult":"SUCCESS",
"provisioningTarget":"Corp AD",
"ticketId":"72619262",
"attributeRequests":[
{
"operation":"Add",
"attributeName":"memberOf",
"attributeValue":"CN=admin,DC=training,DC=com"
}
]
}
]
Here you can see the attributeRequests object lists the accesses provisioned.
Now if you look at the json Sample of get Access Action below (from this page), it has a list of accesses the user has.
{
"accessItems":[
{
"id":"2c9180847fdd00e1017ff5afb9c31f4e",
"name":"CN=AD Access,OU=pod-name,DC=Test",
"type":"entitlement"
},
{
"id":"2c9180867ff523f4017ff5b17ff500af",
"name":"Sales Role",
"type":"role"
},
{
"id":"2c9180887ff4d87e017ff5b1192b010e",
"name":"Access to AD",
"type":"accessprofile"
}
]
}
If you try to relate these 2, you will see that what is specified as attributeValue in the json from Provisioning Trigger corresponds to the name field under accessItems. You should also make sure that the type of the accessItem is entitlement. Once you filter based on this comparison, you should be able to get the id of the accessItem and then remove it by means of Manage Access Action.