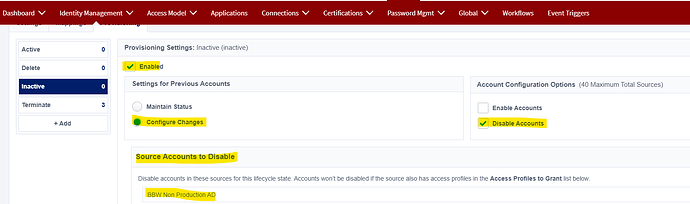
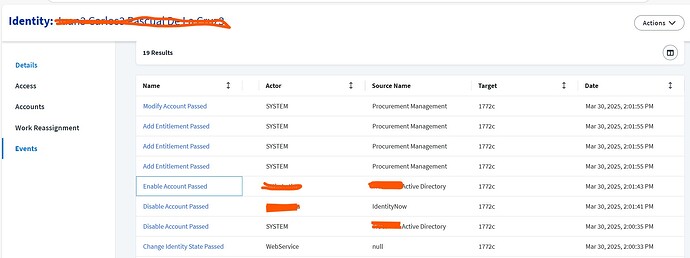
I have created the BeforeProvisioning cloud rule and attached to the AD source for account moves for Disable/Enable and department changes. On IdentityProfile Provisioning tab, Configured the AD source to disable the account on LCS “inactive” on IdentityProfile. The issue is the AD account on target is not getting disabled after the Identity LCS is changed to inactive. Please let me know if any correction required for below rule and how to resolve the issue
<?xml version='1.0' encoding='UTF-8'?> Moves AD account for mover or termination use cases. Also remove additional groupstry {
log.info(“Active Directory Before Provisioning Rule - START”);
List accountRequests = plan.getAccountRequests();
if (accountRequests != null) {
for (AccountRequest accountRequest: accountRequests) {
AccountRequest.Operation op = accountRequest.getOperation();
if (op == null) continue;
String nativeIdentity = accountRequest.getNativeIdentity();
Identity identity = plan.getIdentity();
String currentLCS = null;
String activeOU = null;
String disabledOU = null;
if (identity != null) {
currentLCS = identity.getAttribute(“cloudLifecycleState”);
activeOU = identity.getAttribute(“activeOu”);
disabledOU = identity.getAttribute(“disabledOU”);
}
boolean departmentChanged = false;
if (op.equals(AccountRequest.Operation.Modify)) {
List depAttrReqs = accountRequest.getAttributeRequests("department");
List campAttrReqs = accountRequest.getAttributeRequests("extensionAttribute2");
if ((depAttrReqs != null) && (!depAttrReqs.isEmpty())) {
departmentChanged = true;
} else if ((campAttrReqs != null) && (!campAttrReqs.isEmpty())) {
departmentChanged = true;
}
}
String newOU = null;
/*
Get a new OU only if we are in
Rehire Use Case: (Enable, user LCS is active and user was in the disabled OU)
Mover Use Case: (Modify and user LCS is active)
Termination Use Case: (Disable and user LCS is inactive)
*/
if ("active".equals(currentLCS) && op.equals(AccountRequest.Operation.Enable) &&
disabledOU != null && activeOU != null && nativeIdentity.endsWith(disabledOU)) {
//Rehire Use Case
newOU = activeOU;
} else if ("active".equals(currentLCS) && departmentChanged && activeOU != null) {
//Mover Use Case
newOU = activeOU;
} else if ("inactive".equals(currentLCS) && op.equals(AccountRequest.Operation.Disable)) {
//Termination Use Case
newOU = disabledOU;
}
if (newOU != null && !nativeIdentity.endsWith(newOU)) {
//Account not currently in the proper OU. Put them there
// check if new OU is already set in DISABLE/UPDATE account profiles
List newParentAttrReqs = accountRequest.getAttributeRequests("AC_NewParent");
if ((newParentAttrReqs != null) && (!newParentAttrReqs.isEmpty())) {
for (AttributeRequest attrRequest: newParentAttrReqs) {
attrRequest.setValue(newOU);
}
} else {
accountRequest.add(new AttributeRequest("AC_NewParent", ProvisioningPlan.Operation.Set, newOU));
}
//if campaign/dept is changed, remove all the groups except domain users
if (departmentChanged) {
String domainUsersDN = identity.getStringAttribute("domainUsersDN");
if (!domainUsersDN.isEmpty() && !domainUsersDN.isBlank()) {
List newGroups = new ArrayList();
newGroups.add(domainUsersDN);
accountRequest.add(new AttributeRequest("memberOf", ProvisioningPlan.Operation.Set, newGroups));
}
}
}
}
}
} catch (Exception ex) {
log.error("Active Directory Before Provisioning Rule - Exception occured: ", ex);
log.error("Provisioning Plan: " + plan);
}
log.info(“Active Directory Before Provisioning Rule - END”);
]]>